
Online retailers are losing revenue right under their noses thanks to a devious form of ad injection only visible to infected site visitors.
“I didn’t even know we had a problem,” said Jason LeBoeuf, director of ecommerce at athletics footwear brand Asics.
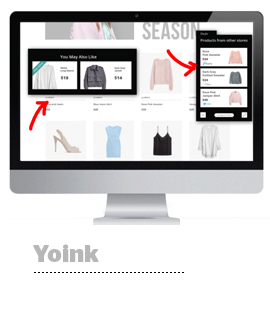
The Asics website was the victim of customer-journey hijacking, a sneaky practice by which malware sitting on a site visitor’s machine entices users to click on unauthorized product ads and links that whisk them away from their original destination to other sites.
It’s primarily a form of ad injection for affiliate marketing. Bad actors bundle the malware within legitimate free software, such as PDF launchers or even antivirus software. When users with an infected device visit a website, they see banners, pop-ups and in-text ads layered on top of existing content that aims to lure them elsewhere.
The malware is designed to bypass server-side web security tools, which allows the ads to hide in plain sight. Only an infected site visitor can see them.
“Every site has pop-ups, and there’s a lot going on,” LeBoeuf said. “These ads can blend into the noise.”
Bad actors often pull legitimate ads from affiliate marketing networks, such as Commission Junction or LinkShare. The visitor doesn’t know the ad isn’t legitimate, and the site owner isn’t any the wiser either, because the malware hijacking the on-site experience is on the visitor’s device or within their own browser.
“We’ve seen customers get pop-up ads featuring competitors, and we’ve even seen ads for our own products coming through our own affiliate partners – but still, these ads are pushing visitors off of our own site,” LeBoeuf said. “I do direct-to-consumer; I don’t want anyone leaving our website.”
Namogoo, a startup that specializes in helping ecommerce sites combat this form of ad injection, estimates that 15-20% of web sessions on ecommerce sites are unwittingly bedeviled by journey hijacking.
Asics is working with Namogoo to retake control of the customer experience on its site. Namogoo’s technology works by neutralizing the malware on an infected user’s machine when that person visits a website. The malware is still there, but it’s blocked from damaging the retailer’s on-site experience.
The number of visitors to Asics.com with infected machines hasn’t changed over time – around 15-20% of all traffic – but the malware’s ability has been compromised.
Since hooking up with Namogoo, Asics has seen its overall conversion rate increase 1-3%. That translates to between $300,000 and $800,000 in recouped revenue, depending on the season.
The hijacking gambit is particularly galling to LeBoeuf because it disrupts the customer experience.
“We put a lot of work into the way our customers flow through the site, from the home page to the category to the product listing through checkout, and all of that work is destroyed when a pop-up swoops in and takes people off that route,” he said. “It may be annoying to them or they might not even understand that the ad isn’t coming from us.”
The malware also messes with the site’s analytics.
“The ecommerce company has no idea that they might have just lost a transaction due to unauthorized content popping up on the screen,” said Chemi Katz, CEO and co-founder of Namogoo. “From their perspective, the customer just bounced or abandoned their cart.”
Namogoo integrates with analytics tools, like Google Analytics or Tableau, so retailers can see the effect of hijacked sessions on site activity.
Although most of the offending ads feature product images and are taken from affiliate networks, some perpetrators also hijack parts of the site that are integral to its functioning.
“In one case, we actually saw malware-hijacked text that redirected users from an ecommerce site’s sign-in link to the home page of its biggest competitor,” said Ohad Hagai, VP of marketing at Namogoo. “That’s definitely not the experience the user expects, and it’s not what the website owner designed.”
This post was syndicated from Ad Exchanger.
More Stories
GSTV Wants To Turn Gas Stations Into A Video Ad Marketplace
Chicken cake marks ten years for Bostock Brothers
Adam Scott Adds ‘Facial Hair Enthusiast’ to His CV in Philips Norelco Campaign